Palo Alto firewalls with dual virtual routers
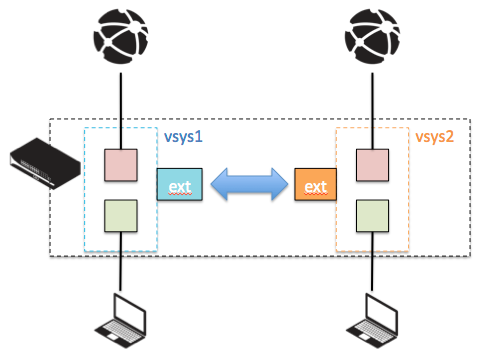
Scenario Overview:
The network is configured with two virtual routers:
- VR1 (SD-WAN VR): Handles all SD-WAN traffic, which includes site-to-site connections and potentially cloud services. This VR is optimized for performance and reliability, leveraging SD-WAN capabilities to manage traffic over multiple links based on policies.
- VR2 (Public Internet VR): Manages all other outgoing and incoming internet traffic. This router is intended for less sensitive, general internet access.
Configuration Details:
Step 1: Setup Virtual Routers
- VR1 – SD-WAN Virtual Router:
- Interfaces: Includes one or more interfaces connected to the SD-WAN appliance or directly to MPLS links, depending on the architecture of the SD-WAN solution. Additionally, it might include internal interfaces that handle traffic to and from the SD-WAN.
- Routing: Configures a default gateway that points towards the SD-WAN network, which dynamically chooses the best route based on the SD-WAN policies.
- VR2 – Public Internet Virtual Router:
- Interfaces: Consists of at least one interface connected to the ISP for internet access and may include local network interfaces that require direct internet access.
- Routing: Sets a default gateway provided by the ISP to route all internet-bound traffic.
Step 2: Configure Routing and Security
- Routing Between VR1 and VR2:
- Although these virtual routers operate independently, routes can be set up in each VR to communicate essential services or for administrative purposes. This might involve static routes directing traffic from one VR to another for specific networks.
- Example: Traffic from the corporate LAN on VR1 needing to access external internet services must route through VR2.
- Security Policies:
- Define security policies in Palo Alto to ensure that only authorized traffic can flow between VR1 and VR2.
- Use zones to segregate traffic, with different policies applied based on the source and destination zones attached to VR1 and VR2.
Step 3: Implement Failover and Redundancy
- Failover Between VRs:
- While each VR has its dedicated path, configuring failover scenarios where, in case of a failure in the SD-WAN links, critical traffic could reroute through the public internet VR as a backup.
- This setup requires careful policy and routing adjustments to maintain security and performance standards.
- Monitoring and Management:
- Continuous monitoring of both virtual routers is crucial to ensure they perform as expected and to detect any issues related to traffic flow, security, or connectivity.
- Implement logging and alerting mechanisms to keep network administrators informed of the status and health of each VR.
Step-by-Step GUI Configuration
Step 1: Define Virtual Routers
- Login to the Firewall Web Interface:
- Access the Palo Alto firewall through your web browser by entering the firewall’s IP address.
- Create Virtual Routers:
- Navigate to Network > Virtual Routers.
- Click Add to create two new virtual routers:
- Name
VR1-SDWANfor the SD-WAN virtual router. - Name
VR2-Publicfor the public internet virtual router.
- Name
Step 2: Configure Interfaces
- Assign Interfaces to Virtual Routers:
- Go to Network > Interfaces.
- Assign the appropriate interfaces to each virtual router:
- For
VR1-SDWAN, assign interfaces that connect to your SD-WAN appliance or service. - For
VR2-Public, assign the interface that connects to your ISP and any other interfaces that require direct internet access.
- For
Step 3: Configure Static Routes
- Set Default Gateways:
- For each virtual router, configure the default route to ensure proper traffic direction:
- VR1-SDWAN:
- Navigate back to Network > Virtual Routers and select
VR1-SDWAN. - Go to the Static Routes tab and click Add.
- Destination:
0.0.0.0/0 - Interface: Select the SD-WAN interface.
- Next Hop: Enter the IP address of the SD-WAN gateway.
- Navigate back to Network > Virtual Routers and select
- VR2-Public:
- Select
VR2-Publicfrom Virtual Routers. - Repeat the steps above but set the Next Hop to the IP address provided by your ISP.
- Select
- VR1-SDWAN:
- For each virtual router, configure the default route to ensure proper traffic direction:
Step 4: Configure Security and Routing Policies
- Create Security Zones and Policies:
- Navigate to Policies > Security to create new rules that govern traffic between the two virtual routers:
- Define new zones for each virtual router, then create policies that allow or deny traffic as necessary.
- You may need to allow specific traffic from
VR1-SDWANtoVR2-Publicfor internet access or administrative purposes.
- Navigate to Policies > Security to create new rules that govern traffic between the two virtual routers:
Step 5: Monitoring and Management
- Set Up Monitoring:
- Use the Monitoring tab on the firewall to set up logging and alerting for traffic across both virtual routers. This will help you track performance and identify issues.

Tech Enthusiast & Knowledge Sharer
I am a passionate technologist dedicated to demystifying the world of networking, cloud computing, and automation. Focusing on simplicity and practicality.
I believe in breaking down complex concepts into understandable and actionable insights.
Pages: 1 2