Understanding Virtual Routers in Palo Alto Firewalls
In Palo Alto firewalls, virtual routers play a crucial role in network layer management by facilitating efficient route determination and packet forwarding across different subnets. These virtual routers operate by obtaining routes through either static configurations manually defined by network administrators or through dynamic routing protocols such as BGP, OSPF, OSPFv3, or RIP.
How Virtual Routers Process Traffic
- Routing Information Base (RIB): Virtual routers maintain a RIB that contains all learned routes, which are either dynamically learned through routing protocols or manually configured as static routes.
- Forwarding Information Base (FIB): When a packet needs to be routed to a different subnet, the virtual router selects the best route from the RIB, places this route into the FIB, and then forwards the packet to the next-hop router specified in this FIB entry. In cases where Equal-Cost Multi-Path Routing (ECMP) is used, all equal-cost paths are included in the FIB to ensure efficient load balancing.
Interface Role and Security
- Interface Types: The firewall’s Ethernet, VLAN, and tunnel interfaces handle the reception and forwarding of Layer 3 packets. The outgoing interface’s role determines the destination zone, influencing how traffic forwarding rules are applied.
- Security Enforcement: As packets are forwarded, the firewall applies relevant security policies based on the rules configured for the traffic’s originating and destination zones.
Inter-Virtual Router Communication
- Routing Between Virtual Routers: Virtual routers can also route packets to other virtual routers within the same firewall. This is typically configured by setting a next-hop in a static route to point to another virtual router.
- Dynamic Routing Across Virtual Routers: To facilitate dynamic routing between virtual routers, loopback interfaces can be created and peered using dynamic routing protocols, with static routes directing traffic between these loopbacks. However, it’s important to note that the firewall supports only direct (single-hop) routing between virtual routers, not multi-hop routing (e.g., from VR A to VR C directly, skipping VR B).
Configuration Flexibility
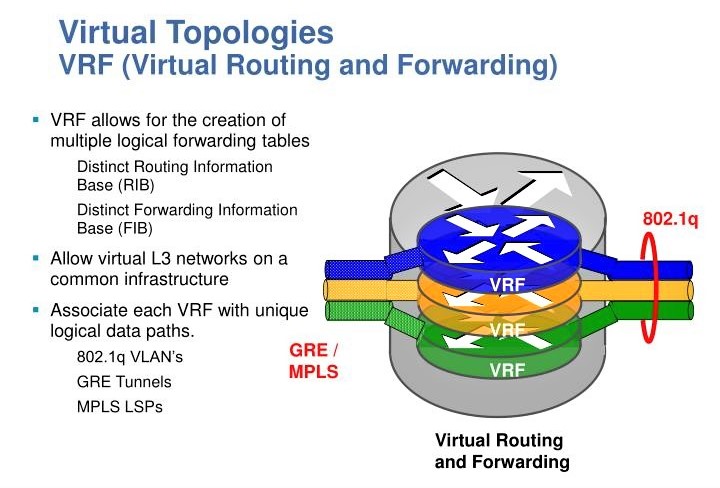
- Multiple Virtual Routers: Administrators can configure multiple virtual routers, each with its distinct set of routes and interfaces. This capability allows for tailored routing behaviors and isolation between different network segments.
Comprehensive Routing Options: Each virtual router can support multiple routing protocols alongside static routes, offering a flexible approach to network traffic management. Despite the variety of specific routes and protocols, a base configuration for each virtual router is essential to establish its operational framework
Mastering Network Segmentation with Virtual Routers in Palo Alto Firewalls
Designing traffic selection and managing isolation in environments with single, dual, and triple virtual router setups in Palo Alto firewalls involves understanding the principles of traffic flow, segmentation, and policy enforcement. Here’s a comprehensive breakdown for different designs:
Single Virtual Router Design
Traffic Selection and Isolation
- Traffic Isolation: In a single virtual router setup, all interfaces, whether Ethernet, VLAN, or tunnel, are managed by the same virtual router. This design simplifies routing but offers limited traffic isolation since all routes are known to the same routing instance.
- Traffic Filtering: Use security policies to filter traffic between zones. Each interface on the virtual router can be assigned to a specific zone, and inter-zone policies can control the traffic flows.
Interface Connections
- Connecting Interfaces: All interfaces (Ethernet, VLAN, tunnel) are part of the same routing table, allowing straightforward connectivity. Routes and policies dictate the traffic flow, ensuring that packets reach their designated destinations based on the best path in the routing table.
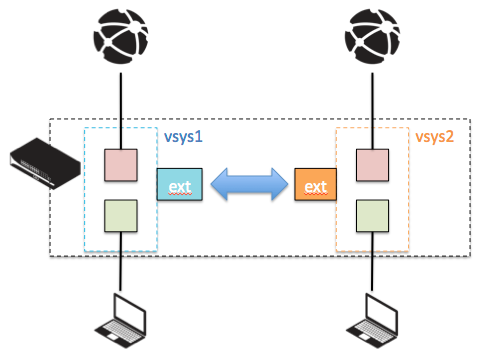
Dual Virtual Router Design
Traffic Selection and Isolation
- Enhanced Isolation: With two virtual routers, you can separate traffic types or network segments more distinctly. For example, one router could manage internal traffic, while the other handles external or WAN traffic.
- Traffic Filtering: Implement inter-virtual router routing by defining static routes pointing to the next-hop addresses or interfaces managed by the opposite virtual router. Security policies must be configured to allow traffic between zones associated with different virtual routers.
Interface Connections
- Connecting Across Virtual Routers: If interfaces on different virtual routers need to communicate, static routes are used to direct traffic from one virtual router to the next. For example, a route in VR1 could direct traffic destined for an external network to an interface managed by VR2, which handles WAN traffic.
Triple Virtual Router Design
Traffic Selection and Isolation
- Maximum Isolation: Three virtual routers allow for even more granular control over traffic flows—ideal for separating sensitive systems, managing multiple external connections, or isolating developmental environments from production.
- Traffic Filtering: Routing between three virtual routers requires careful planning. Since Palo Alto firewalls support only direct routing between virtual routers, complex environments might necessitate the use of a common transit network or dedicated interfaces on each virtual router that connect through physical or logical links.
Interface Connections
- Multi-Router Connectivity: Establish connectivity through shared networks or dedicated interfaces. For example, you could have a common VLAN or a loopback interface that all virtual routers can route through, or use direct static routes if the topology allows.
Virtual Router Configuration
Step-by-Step Guide:
- Log into the Firewall: Access the Palo Alto firewall through the web interface or CLI.
- Navigate to Network Settings: Go to the ‘Network’ tab and select ‘Virtual Routers’.
- Create a New Virtual Router: Click on ‘Add’ to create a new virtual router. Name it appropriately, e.g., Local-VR for local network management.
- Assign Interfaces: Assign the interfaces that will participate in this virtual router. This might include LAN interfaces, tunnel interfaces, and VLANs.
- Configure Routing Protocols: Set up routing protocols as necessary. For example, if you’re using OSPF:
- Go to the ‘OSPF’ tab within the virtual router settings.
- Enable OSPF, configure the Area ID, and add the network statements to advertise routes.
Virtual Router Traffic Selection
Traffic is directed to a virtual router based on interface assignments and routing decisions. Configure routing policies and rules that determine how traffic is handled:
- Static Routes: Define static routes if specific traffic management is needed without dynamic routing protocols.
- Security Policies: Set up firewall rules that allow or deny traffic based on the source and destination zones, associated with different virtual routers.
Scenario: Dual Virtual Router Setup
Configuration of Two Virtual Routers:
- Local Plan Virtual Router (Local-VR): Manages internal networks and site-to-site VPNs.
- WAN Virtual Router (WAN-VR): Manages traffic going to and from the WAN, including internet access.
Configuring Communication Between Two Virtual Routers:
- Static Routes for Inter-Router Communication:
- On Local-VR, add a static route to the WAN networks with WAN-VR as the next hop.
- On WAN-VR, add a static route back to the local networks managed by Local-VR.
- Security Policies:
- Create policies that allow necessary traffic between the networks managed by Local-VR and WAN-VR.
Enabling Tunnel Interfaces:
- Create a Tunnel Interface on Local-VR:
- Navigate to ‘Interfaces’ and create a new tunnel interface, e.g., tunnel.1.
- Assign it to Local-VR and configure IP addressing and other parameters.
- Define the tunnel settings, such as type (IPsec), and configure the IPsec profile.
Routing Techniques:
- Dynamic Routing: Use OSPF or BGP for dynamic exchange of routes between Local-VR and WAN-VR.
- Policy-Based Routing (PBR): If specific traffic must bypass normal routing:
- Create a PBR policy that matches traffic based on criteria like source IP and directs it to a specific next-hop (e.g., from Local-VR to WAN-VR).
Introduction to Virtual Routers and SD-WAN Integration
Virtual routers in Palo Alto firewalls allow for the segmentation of different network areas, supporting both static and dynamic routing protocols. Integrating an SD-WAN gateway with a virtual router enhances routing capabilities, providing intelligent path selection, load balancing, and improved reliability.
Detailed Virtual Router Configuration using GUI
Creating and Configuring Virtual Routers
- Login and Access the Virtual Routers:
- Open your web browser and log into the Palo Alto firewall’s web interface.
- Navigate to Network > Virtual Routers and click Add to create a new virtual router.
- Configure Virtual Router (Local-VR and WAN-VR):
- Name the virtual routers appropriately. For instance, Local-VR for local network management and WAN-VR for WAN traffic management.
- In each virtual router’s configuration page, add and assign interfaces. For Local-VR, include internal interfaces and for WAN-VR, add external facing interfaces.
- Setting Up Routing Protocols:
- Select the virtual router, go to the Routing Table tab, and add static or dynamic routes as required.
- For dynamic routing like OSPF, navigate to the OSPF tab within the virtual router and configure the OSPF settings.
Traffic Selection and Advanced Routing Configurations
- Configure Security and Routing Policies:
- Go to Policies > Security to define rules that control traffic flow between the interfaces managed by different virtual routers.
- Use the Policy Based Forwarding section to create rules for directing traffic based on specific criteria, like source or destination IP.

Tech Enthusiast & Knowledge Sharer
I am a passionate technologist dedicated to demystifying the world of networking, cloud computing, and automation. Focusing on simplicity and practicality.
I believe in breaking down complex concepts into understandable and actionable insights.