Explore technology
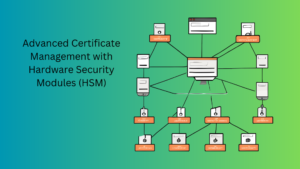
Advanced Certificate Management with Hardware Security Modules (HSM)
Introduction Hardware Security Modules (HSM) provide enhanced security for managing cryptographic keys and certificates. This post provides a detailed, step-by-step guide on using HSMs with Palo Alto Networks firewalls to secure private keys and manage certificate encryption effectively. Importance of HSMs in Certificate Management HSMs are essential for: Steps to Configure HSM
Troubleshooting Palo Alto Certificate Issues
Introduction Certificates are a cornerstone of network security, but issues with certificates can lead to significant disruptions and vulnerabilities. This post provides a detailed, step-by-step guide to troubleshooting common certificate-related issues on Palo Alto Networks firewalls, ensuring that your network remains secure and operational. Importance of Troubleshooting Certificate Issues Properly troubleshooting certificate
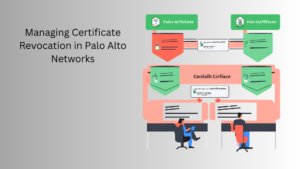
Managing Certificate Revocation in Palo Alto Networks
Introduction Managing the lifecycle of certificates, including revocation and renewal, is crucial for maintaining network security. This post provides a detailed, step-by-step guide on managing certificate revocation in Palo Alto Networks, ensuring that revoked certificates are properly handled to maintain secure communications. Importance of Certificate Revocation Certificate revocation is essential for: Steps
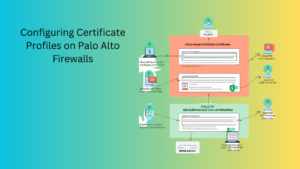
Configuring Certificate Profiles on Palo Alto Firewalls
Introduction Configuring certificate profiles on your Palo Alto Networks firewall is essential for ensuring secure communications and proper certificate management. This post provides a detailed, step-by-step guide on setting up and managing certificate profiles to ensure secure communications and proper certificate usage. Importance of Certificate Profiles Certificate profiles are crucial for: Steps
How to Generate and Install Palo Alto Certificates
Introduction Properly generating and installing certificates on your Palo Alto Networks firewall is crucial for ensuring secure communications and managing network security effectively. This post provides a detailed, step-by-step guide on how to generate self-signed certificates and install CA-signed certificates on Palo Alto firewalls. Importance of Certificates in Network Security Certificates are
Understanding Palo Alto Certificates: An Introduction
Introduction Certificates play a crucial role in ensuring secure communications within networks. In the context of Palo Alto Networks, certificates are used for various security functions such as SSL/TLS decryption, secure management access, and VPNs. This post provides an overview of the different types of certificates used in Palo Alto Networks and
“Experience Peak Visibility and Performance with Zscaler ZDX Application Monitoring”
Zscaler ZDX Application Monitoring emerges as a robust solution, empowering organizations to proactively monitor, analyze, and optimize application performance across the network. Key Features: Implementation Strategies: Application Monitoring To configure applications, we need to follow below steps: From the top of the page, click on Probes and then find the application which
Embracing Error: Teaching AI to Learn from Mistakes
Introduction Artificial Intelligence (AI) and machine learning represent transformative technologies that decipher complex patterns within massive datasets to predict outcomes and make decisions. Traditionally, these systems are honed during training phases to minimize errors—an approach ingrained in their developmental fabric. Yet, this method primarily focuses on achieving accuracy rather than exploring the